Tech
-

Ethical Biometrics High Road Should Be Easy, Yet Many Identity Service Providers Struggle
Biometrics can be used to authenticate people. It is simple and easy. It isn’t without its difficulties. These challenges include security, reliability, and applications. We will be discussing the reliability and security concerns associated with biometrics, and we will also discuss possible solutions. Biometrics Biometrics can be used for authentication and identification in various situations. Biometrics implementation must be secured and adhere to certain…
Read More » -

8 Reasons Why You Should Hire a Professional Web Developer
Websites are an integral part of businesses these days, and if you’re starting one or already have one, the last thing you want to do is create your own website from scratch and not get it right. This article will give you eight reasons why you should hire a professional web developer, so that your website works as efficiently as…
Read More » -
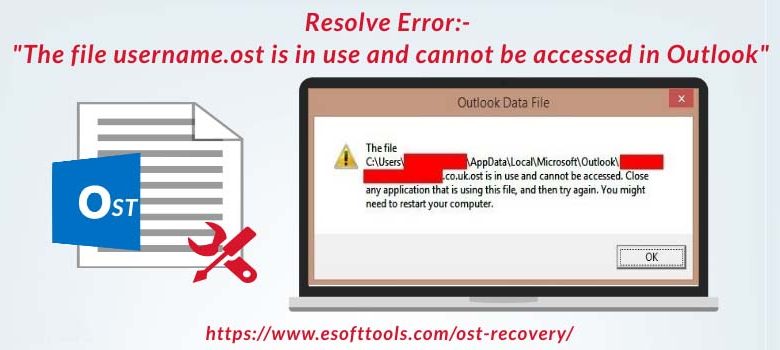
Outlook OST File Is In Use and Cannot Be Accessed Error
Summary: OST file belongs to MS Outlook and issues with OST file threw errors like ‘Outlook abc.ost file is in use and can’t be accessed.’ To resolve this type of error, the faulty OST data file to PST format must be converted. However, to fix this Outlook error, multiple methods are there. In today’s post, we will talk about all…
Read More » -

How to Hire a Python Developer: 9 Key Qualities to Look For
The following are the 9 most important qualities to look for when hiring a python developer. If you’re looking to hire someone to help you with your python programming, it’s essential that you be sure this person has these qualities and characteristics. Don’t settle for less when it comes to hiring a python developer, as this can cause problems further…
Read More » -

How to Unlock Password Protected PowerPoint VBA File? Complete Information
This article will be of the utmost use to you if you are planning to erase the PowerPoint VBA password since we provide realistic options for carrying out the complete procedure without losing any data. Let’s talk about some other crucial details before detailing this technique. Developers and programmers sometimes lose track of the password for a PowerPoint Presentation VBA…
Read More » -

The Future of Desktop Software Development
In early times when people used desktop applications. But in recent technology and desktop software development firms have pushed them out; new development of the desktop application has taken place with more popularity; Trello, Azure, and Wrike are examples of web-based applications that have expanded into desktops. Some applications have more features, some are more resourceful, and some are equitably…
Read More » -

The Impact of Technology on Travel Agencies
Planning a business trip or holiday escapade used to require knocking on the doors of every travel agency in your neighborhood. Afterward, you simply asked for prices, compared them between agencies, made your maths, and returned to the chosen agency to finish the trip. You might be able to handle everything by phone, then collect your tickets and travel plans…
Read More » -

Why and How should Test Automation be implemented in Agile?
There should be a workable strategy put in place that can scale up the test automation activities in an agile environment. Upon that, the implementation of test automation in agile should streamline and speed up the testing processes, while focusing on quick and productive deliverables. The assigned teams must put in tactical efforts to bring out the best of agile…
Read More » -

Why Does Your Cell Phone Need a Screen Protector?
The display of a smartphone is the main thing that we need to operate it daily. As we have all the touchscreen smartphones today everything is operated through the display itself. To make sure that the display is protected always were introduced, screen protectors or screen guards. However, the screen guard screen protector doesn’t come along with any mobile phone…
Read More » -
How To Pick The Leading Cryptocurrency Wallet In 2022
To purchase cryptocurrency, you must create a cryptocurrency wallet; however, which is the best wallet for beginners? The answer will vary from individual to individual. However, regardless of individual circumstances, security should always guide the selection of cryptocurrency wallets. In this article, we examine these security concerns about the custody and classification of cryptocurrency wallets. What Is The Definition Of…
Read More »
